The solution described in the article is not fully working to the level it satisfies the author. It’s a continuous effort to come up with the best solution that meets both dev and ops requirements.
Me
The problem
I am trying to create a security group using Power Automate using the Microsoft Entra ID connector.
https://learn.microsoft.com/en-us/connectors/azuread/#create-group

Microsoft Entra ID is an Identity and Access Management cloud solution that extends your on-premises directories to the cloud and provides single sign-on to thousands of cloud (SaaS) apps and access to web apps you run on-premises.
https://learn.microsoft.com/en-us/connectors/azuread/
To use this integration, you will need access to a Microsoft Entra ID account with sufficient privileges. To make a connection, select Sign In. You will be prompted to provide your account information and follow the remainder of the screens to create a connection.
To use the Microsoft Entra ID connector, the account needs to have the following administrator permissions:

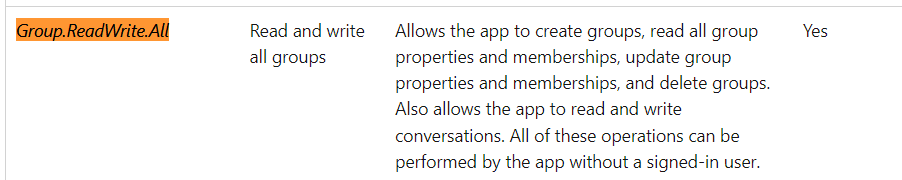
Group.ReadWrite.All
User.ReadWrite.All
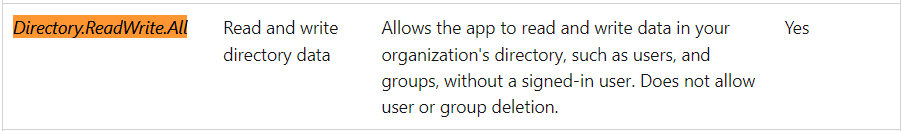
Directory.ReadWrite.All
To create a security group we need
Group.ReadWrite.All
OR
Directory.ReadWrite.All
The connector requires
Group.ReadWrite.All
AND
Directory.ReadWrite.All
There is a clear difference between these two which makes us want to choose the Directory.ReadWrite.All permission (deleting security groups doesn’t sound right so, no)
Permission references: https://learn.microsoft.com/en-us/graph/permissions-reference
Assumption
Let’s assume there is a way to limit the connector permissions via the enterprise app it uses to perform the actions on a user’s behalf.
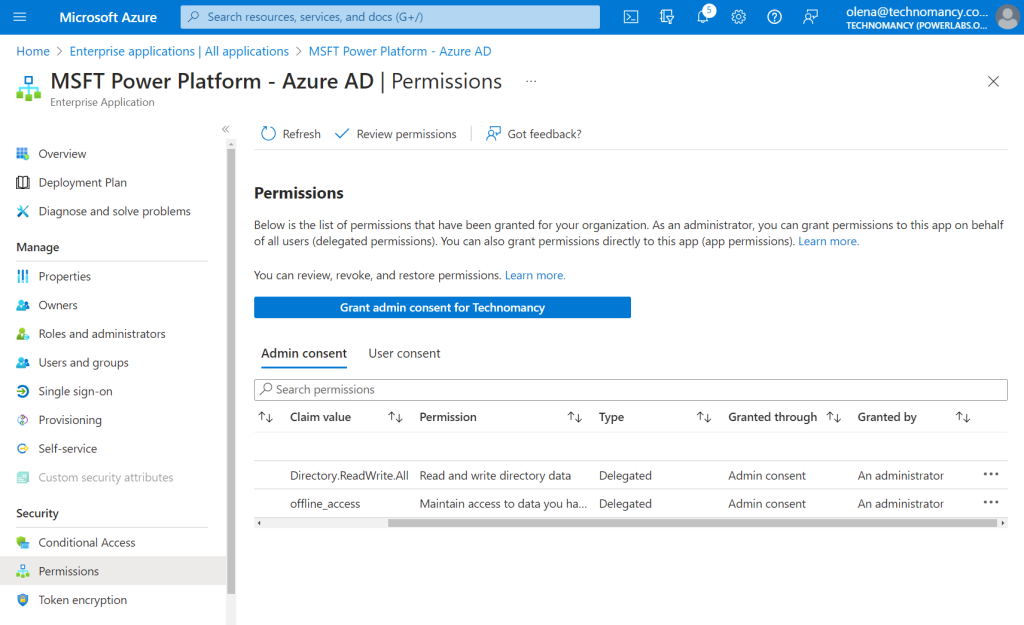
The app gets created auto-magically by the connector. You can find it under Enterprise applications on the Azure portal:
The original set of permissions:
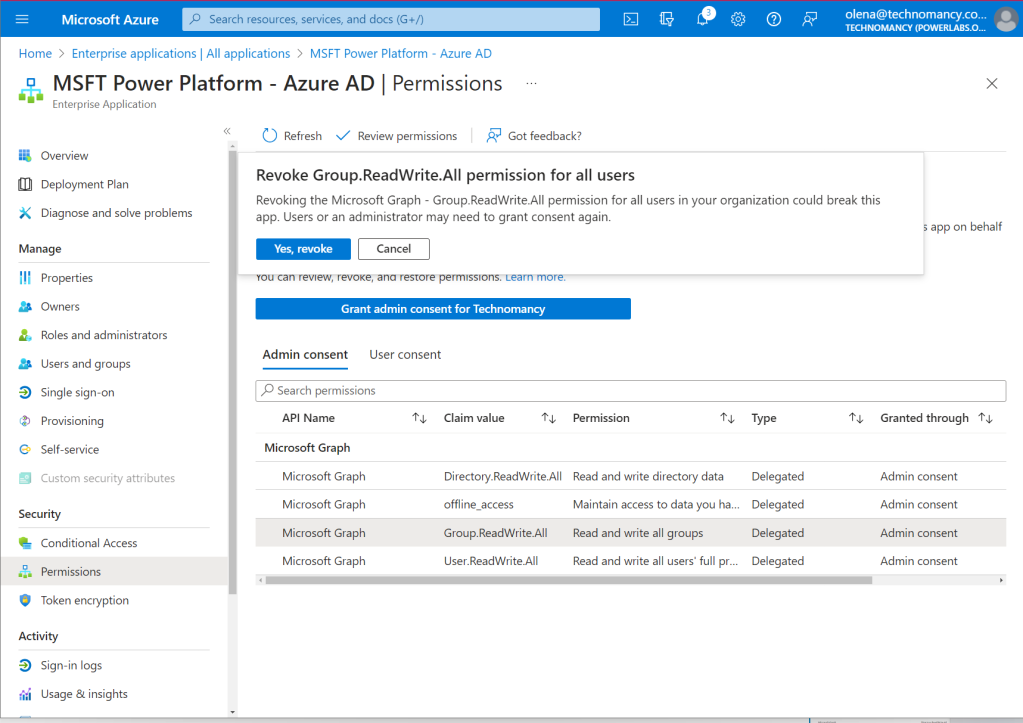
We want something much lighter for the permission list. Something like this:
Set up
I created a new user in my organisation. Peter Pan doesn’t have any admin privileges or super security roles. So it will be good for the testing.
Testing
I created and tested a Flow and then shared it with Peter Pan:
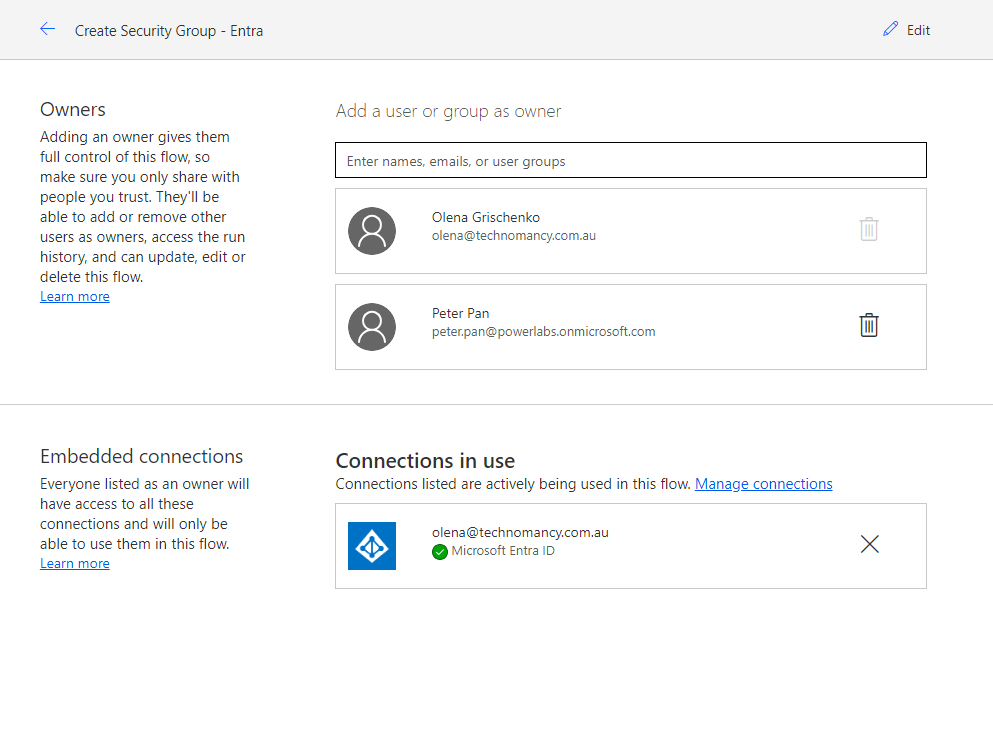
Although Peter has access to my connection I want to create another connection just for him.
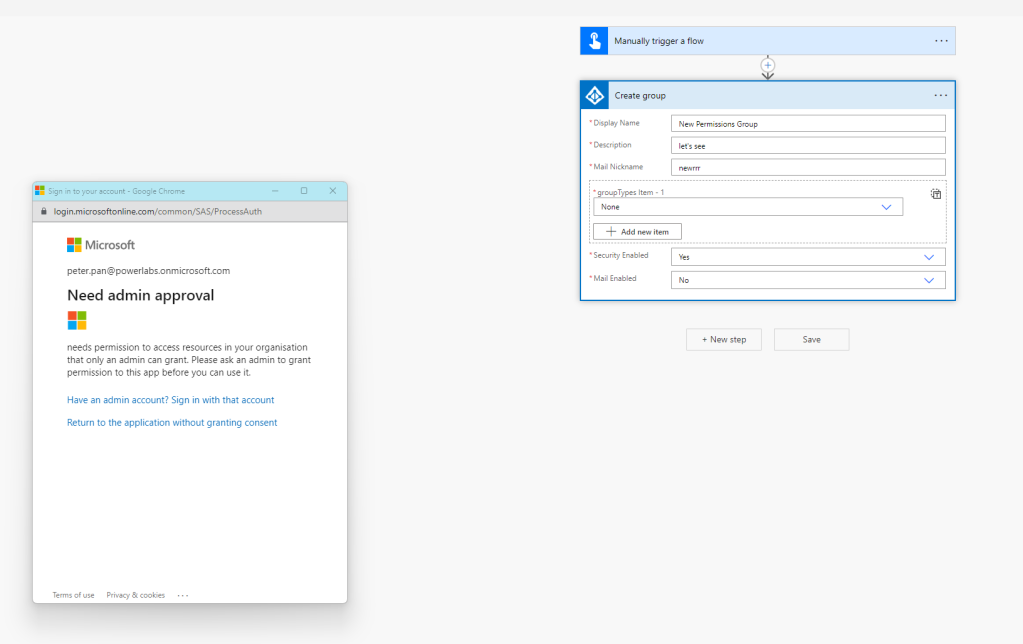
To give the admin approval I had to log in under my admin account.
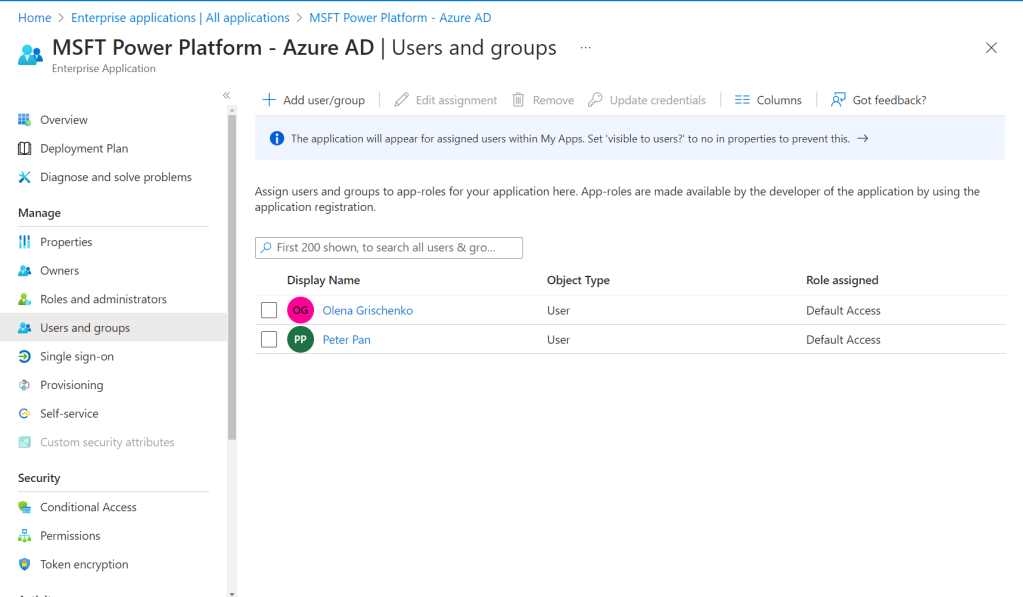
Now Peter is listed as a user of the Entra ID app.
Unfortunately, it reverted my changes and added back the permissions I tried to remove.

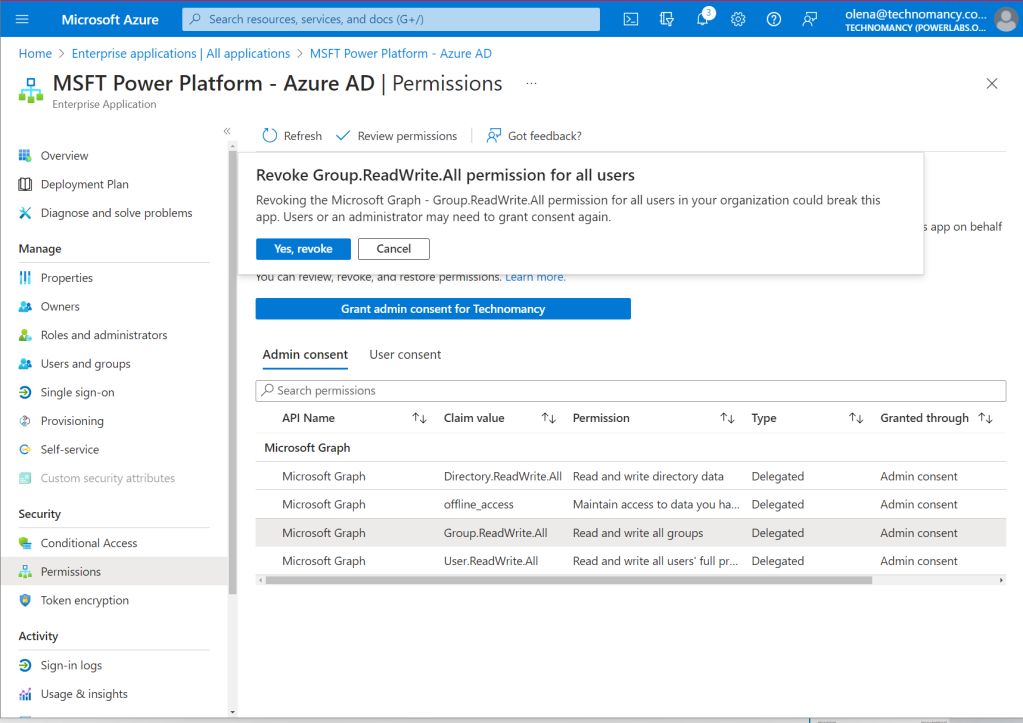
Seriously, I didn’t ask for it!

After removing the excessive permissions for the second time I run the Flow to make sure the connection is working. It is working!
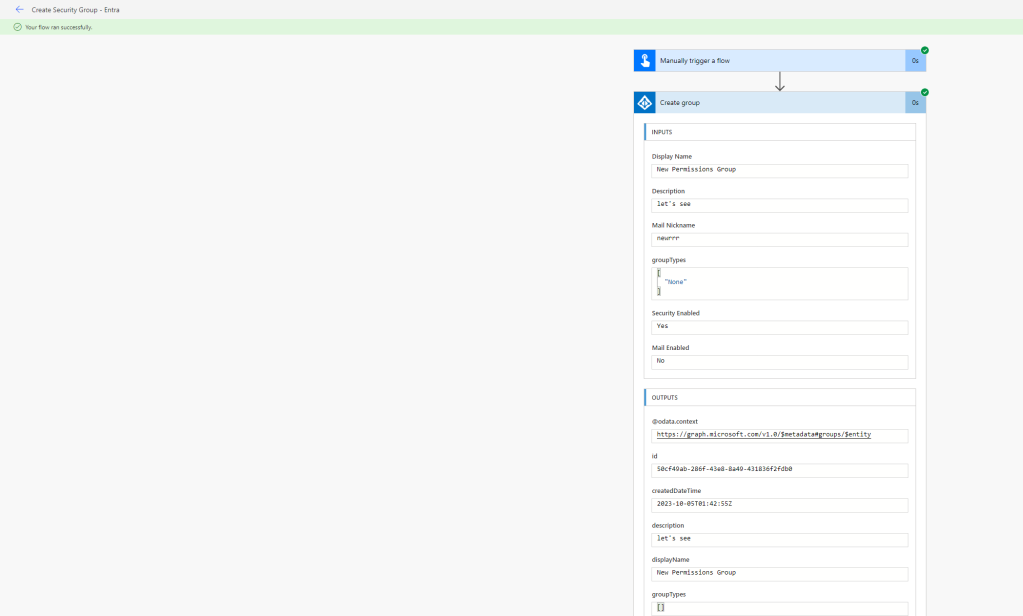
The group was created and looks the way it is supposed to look. So – Yay!
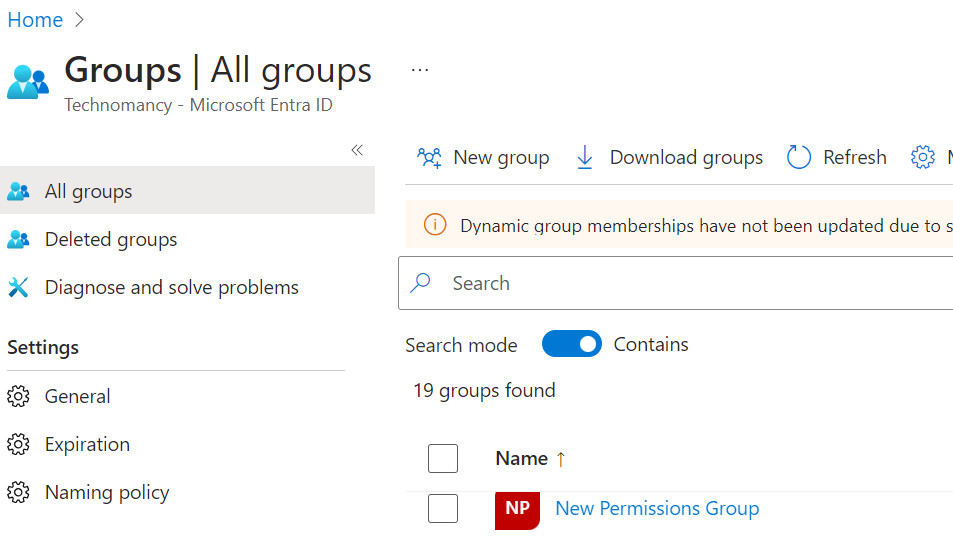
Does it mean we won? Yeah… Nah!
If we need to create another connection or another user needs to create another connection it will get us to the same authentication/authorization flow. Which is very unfortunate!
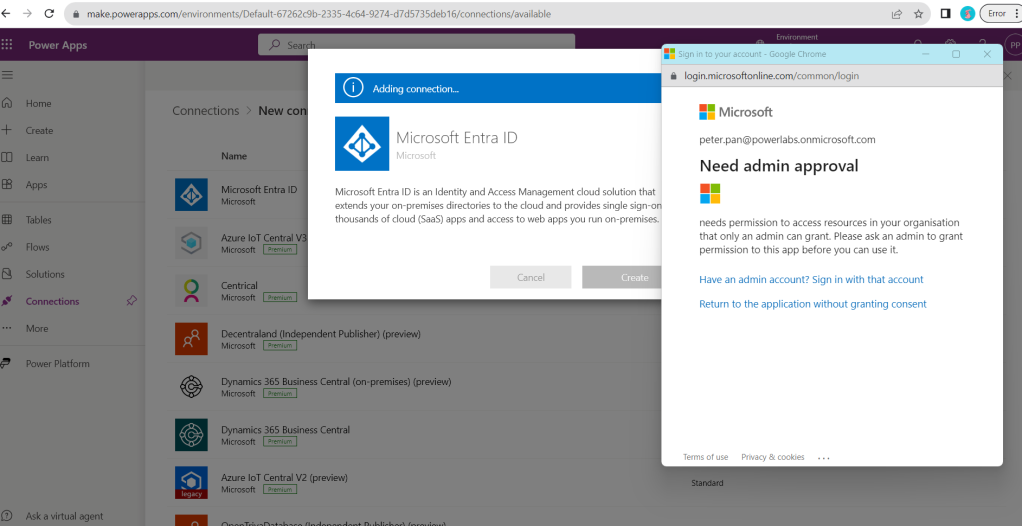
Microsoft! Why?!


