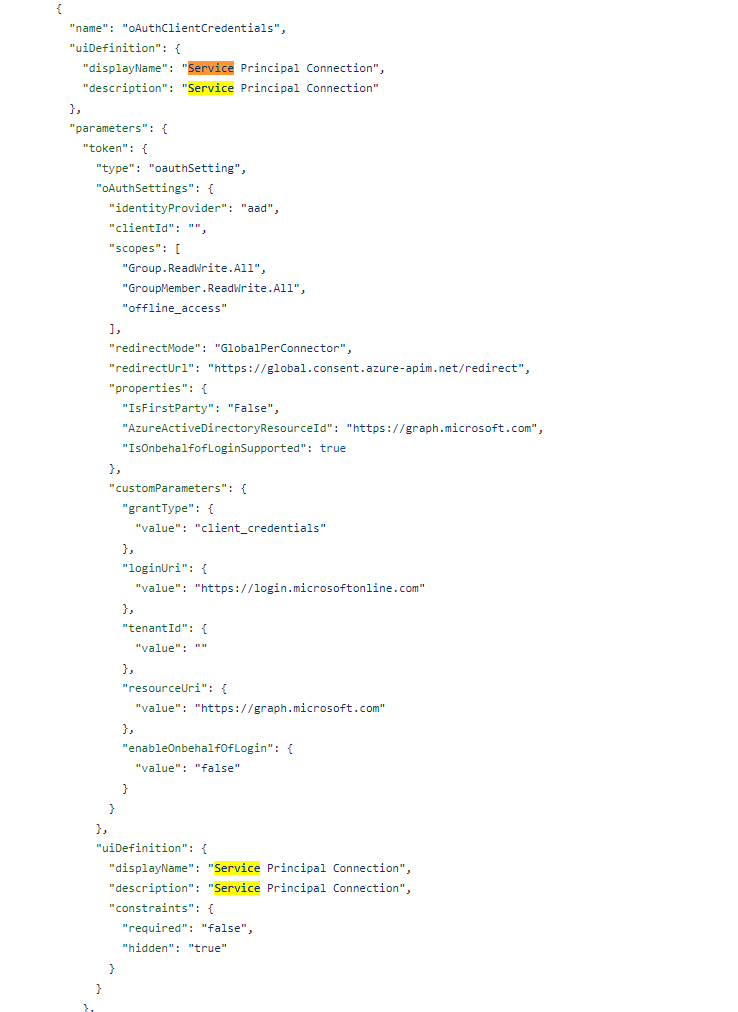
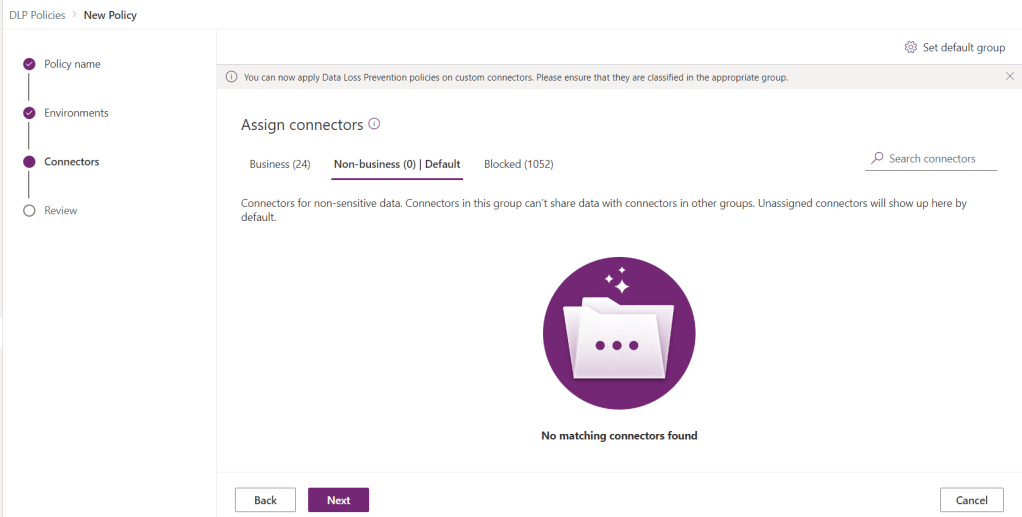
Extending a warm welcome to the Makers starting on the environment is a wonderful idea, especially as Christmas is approaching. We won’t miss the opportunity to send them some heartfelt greetings.
It’s very easy to do for Managed Environments. If you are not familiar with the concept, this is the idea:
Managed Environments is a suite of premium capabilities that allows admins to manage Power Platform at scale with more control, less effort, and more insights. Admins can use Managed Environments with any type of environment. Certain features can be configured upon enabling a Managed Environment. Once an environment is managed, it unlocks additional features across the Power Platform.
Microsoft docos
So we like to display “Maker welcome content” for the Makers. How do we do this?
If you are like me, not believing in reading docos😈, you won’t go here to read this: https://learn.microsoft.com/en-gb/power-platform/admin/welcome-content
You will go straightaway to the Managed Environment settings.
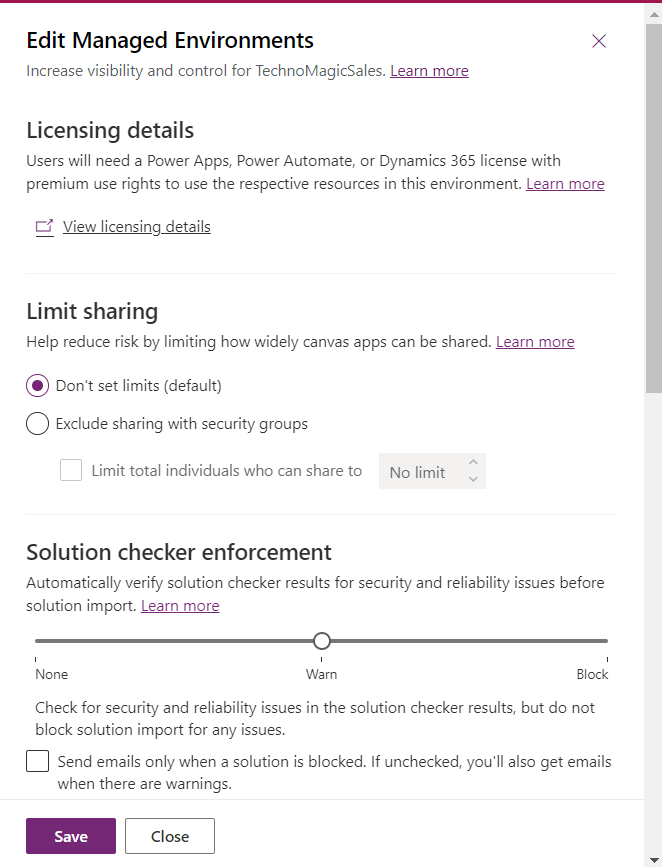
Where you will see this. A plain textbox for the message!
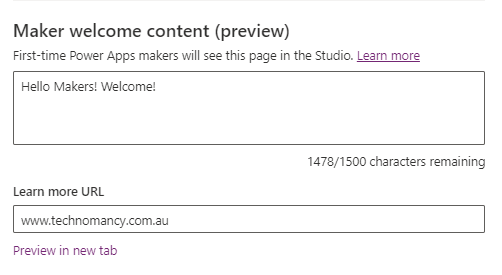
What do we do with it?! How do I make it look awesome for my Makers?!


You may even start crying like I did. But wait for it.
Some Christmas magic is about to happen to us 🪄. (But only to the Makers who’s been good this year 😉
Bad news – you can’t use HTML to make your message look pretty. Good news…
…You can use Markdown!
WTF is Markdown?
Here: https://www.markdownguide.org/getting-started/#what-is-markdown
Markdown is a lightweight markup language that you can use to add formatting elements to plaintext text documents. Created by John Gruber in 2004, Markdown is now one of the world’s most popular markup languages.
Editor
Basic syntax: https://www.markdownguide.org/basic-syntax/
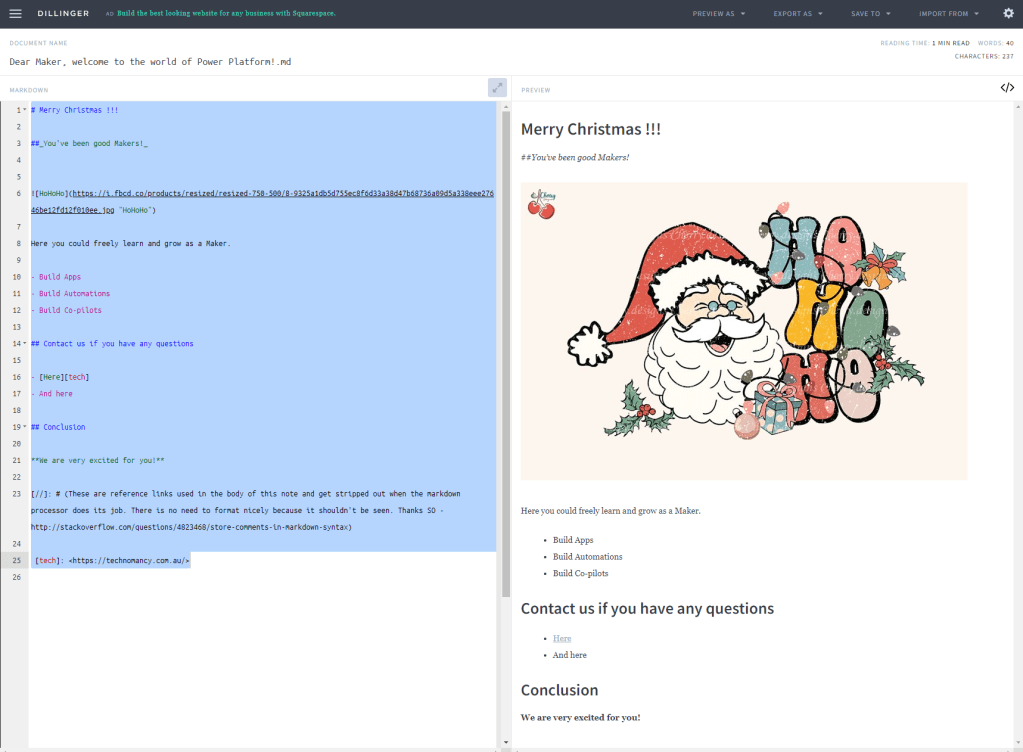
Santa Welcome Message (Markdown)
# Merry Christmas !!!
##_You've been good Makers!_

Here you could freely learn and grow as a Maker.
- Build Apps
- Build Automations
- Build Co-pilots
## Contact us if you have any questions
- [Here][tech]
- And here
## Conclusion
**We are very excited for you!**
[//]: # (These are reference links used in the body of this note and get stripped out when the markdown processor does its job. There is no need to format nicely because it shouldn't be seen. Thanks SO - http://stackoverflow.com/questions/4823468/store-comments-in-markdown-syntax)
[tech]: <https://technomancy.com.au/>How do I test it?
This is an awesome editor for you to test the results of your creativity!
Now we will copy the code to the “plain” textbox in the settings.
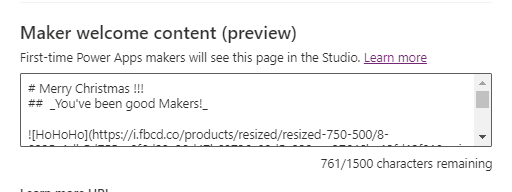
Clicking on Preview in new tab…Awesome!
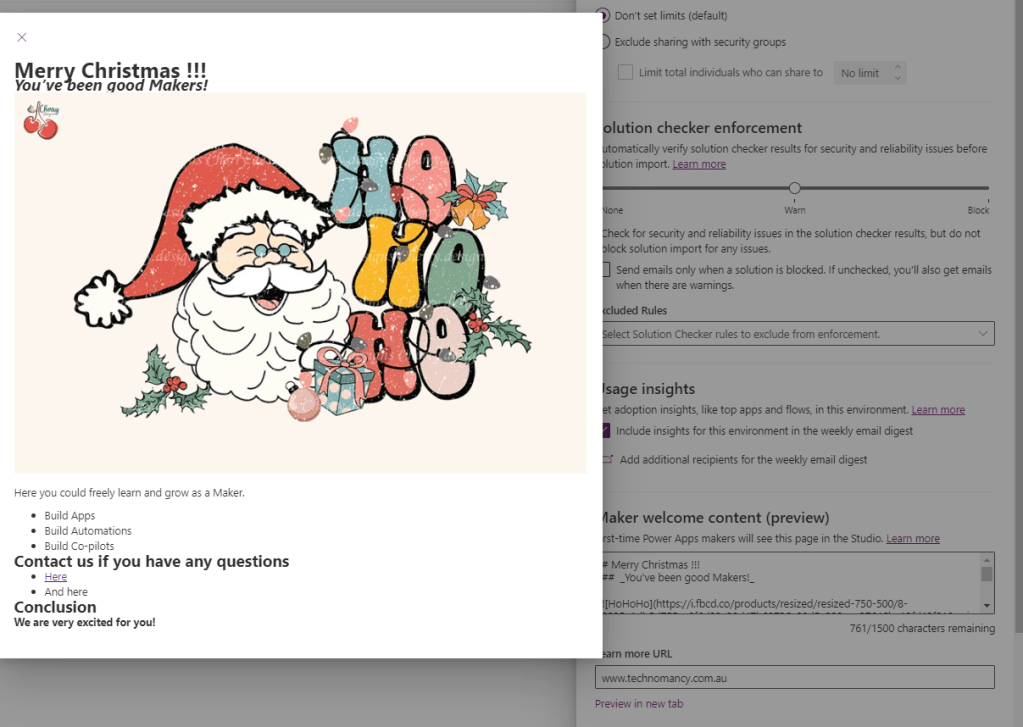
And this is what our Makers will see when they enter the Maker portal on their environment:
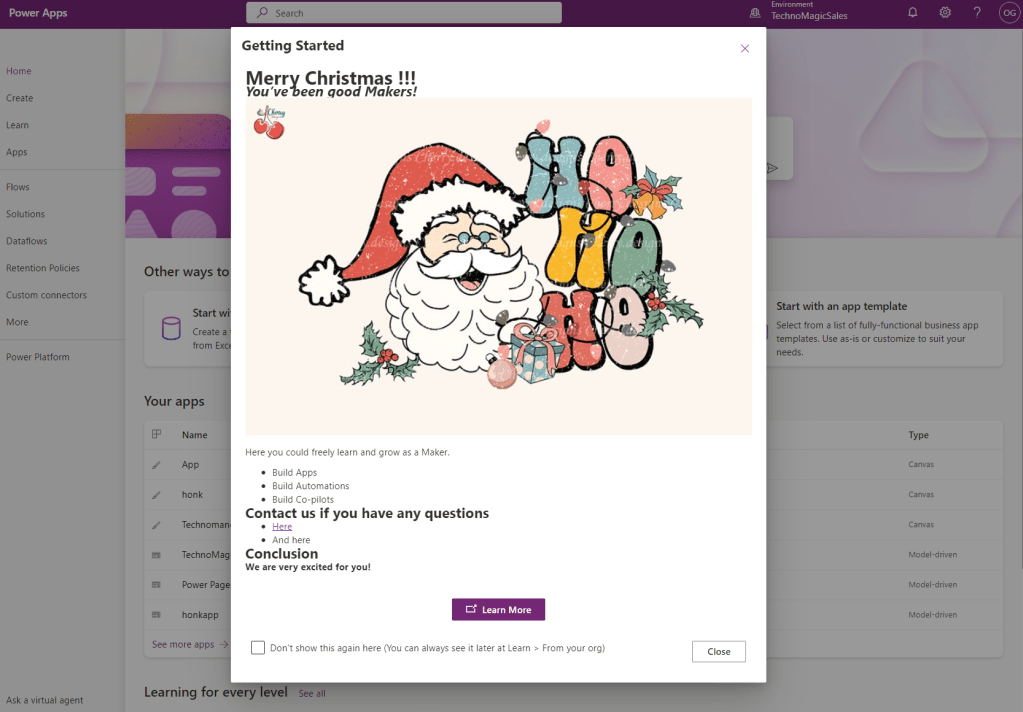
Christmas Miracle 🎅
(OMG, now ChatGPT has stolen the joy of using emojis How could you?! 😡)
(This content is original and generated by a human)